Overview of Policies
I recently came across an interesting blog article from o365blog.com by Dr. Nestori Syynimaa. The premise of the article, and what I’ll be discussing today, show how you can easily bypass Microsoft Teams’ policies by sending an auto response post http call using an app like Fiddler. What this finding shows us is that Microsoft Teams applies its policies on the on the client layer, making it easy to spoof the policies, which I will demonstrate below.
How to Modify Policies
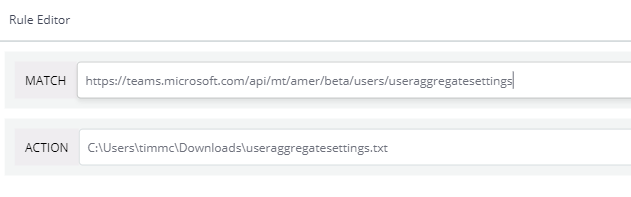
To begin, I fire up Fiddler and enable live traffic capturing. I then fire-up Microsoft Teams and get Fiddler to start listening for calls from the Teams client. The client makes a number of calls, but there are a few calls which interest me and those are the calls that end in “users/useraggregatesettings”. Viewing the body of one of these calls I came across a massive slew of settings and policies being applied on the client layer. Below I’ve listed the messaging policies I can see in the body. The policies you see here will differ from tenant-to-tenant depending on how the policies have been configured in the Microsoft Teams admin center.
"messagingPolicy": {
"value": {
"allowUserEditMessage": true,
"allowUserDeleteMessage": true,
"allowUserChat": true,
"allowGiphy": true,
"giphyRatingType": "Moderate",
"allowGiphyDisplay": true,
"allowPasteInternetImage": true,
"allowMemes": true,
"allowStickers": true,
"allowUserTranslation": true,
"allowUrlPreviews": true,
"readReceiptsEnabledType": "UserPreference",
"allowImmersiveReader": true,
"allowPriorityMessages": true,
"audioMessageEnabledType": "ChatsAndChannels",
"channelsInChatListEnabledType": "DisabledUserOverride",
"allowRemoveUser": true,
"allowSmartReply": true,
"chatPermissionRole": "Restricted"
}
}So to fully test Dr. Syynimaa’s findings I created a text file and copied all these policies into the file, saving it locally. Then using Fiddler, I created an auto response to match these “useraggregatesettings” and replace them with my text file.
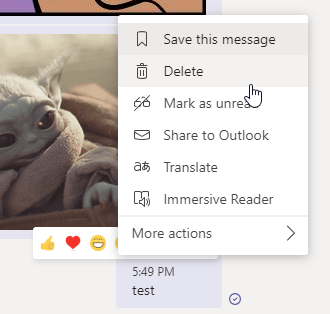
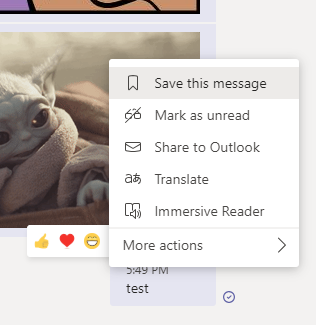
Before running this auto response, I modified the text file by removing the allow delete messages policy from the messaging policy area. By removing the policies you are essentially setting the boolean value for said policy to false. Once removed, I quit Microsoft Teams and relaunched it. In the screenshots below I highlight the before and after message context menu, showing you that the delete action no longer exists after removing the policy.
For comparison sake, I have also included the JSON of the original and modified message policy. The JSON below is the original policy.
"messagingPolicy": {
"value": {
"allowUserDeleteMessage": true,
"allowUserChat": true,
"allowGiphy": true,
"giphyRatingType": "Moderate",
"allowGiphyDisplay": true,
"allowPasteInternetImage": true,
"allowMemes": true,
"allowUserTranslation": true,
"allowUrlPreviews": true,
"readReceiptsEnabledType": "UserPreference",
"allowImmersiveReader": true,
"allowPriorityMessages": true,
"audioMessageEnabledType": "ChatsAndChannels",
"channelsInChatListEnabledType": "DisabledUserOverride",
"allowRemoveUser": true,
"allowSmartReply": true,
"chatPermissionRole": "Restricted"
}
}The message policy below is the modified policy (“allowUserDeleteMessage” has been removed to set it to false).
"messagingPolicy": {
"value": {
"allowUserChat": true,
"allowGiphy": true,
"giphyRatingType": "Moderate",
"allowGiphyDisplay": true,
"allowPasteInternetImage": true,
"allowMemes": true,
"allowUserTranslation": true,
"allowUrlPreviews": true,
"readReceiptsEnabledType": "UserPreference",
"allowImmersiveReader": true,
"allowPriorityMessages": true,
"audioMessageEnabledType": "ChatsAndChannels",
"channelsInChatListEnabledType": "DisabledUserOverride",
"allowRemoveUser": true,
"allowSmartReply": true,
"chatPermissionRole": "Restricted"
}
}Something to point out is that message policies are not the only policies you can modify. You can also modify the following:
- Admin settings
- Tenant settings
- Resource settings
- Meeting policy
- Calling policy
- Client settings
- Teams and Channels Policy
- Education assignment app policy
- Targeting policy
- Feedback policy
Undoing a Custom Admin Policy
So its all well and good that you can set policies to false, but can you undo custom policies that were created in the Teams admin center? Well to test that, I created a custom messaging policy that I applied to the account I’m using for testing. The policy we would like to change is for our user to be able to edit sent messages. As you can see below, the policy, Edit sent messages, is currently turned off.
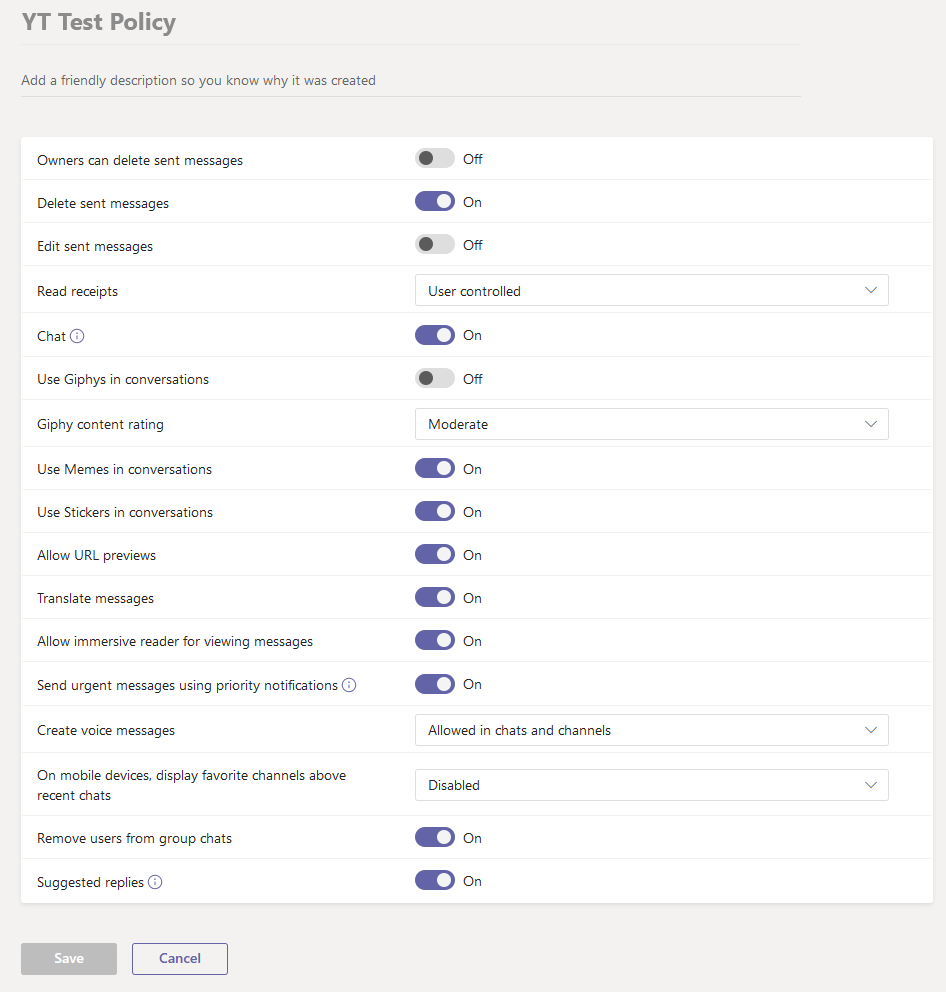
You will notice that when you launch the Teams client with the new custom policy that the edit sent message policy will no longer appear in the JSON body, thus being set to false. To turn it back on, all we simple have to do is add the policy into the text document that we are using in our auto response and voila, you now have the ability to bypass our test policy (see screenshot below).
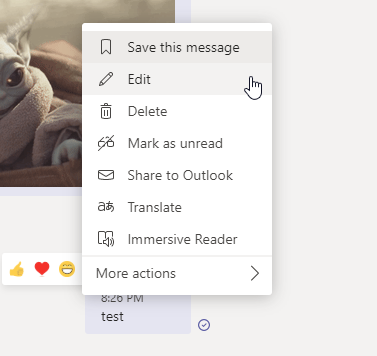
Why do this matter?
So you’re probably asking yourself, why does this matter. What you need to be aware of is that even though these policies are there for admins to help control Teams features for certain users, these policies should NOT be used as security measures for your organization.
